How to implement a single sign-on solution to authenticate users onto the HPE GreenLake edge-to-cloud platform
November 29, 2023Enterprises looking to use HPE GreenLake for Private Cloud Enterprise can benefit from the use of SSO, as it has been integrated onto the HPE GreenLake edge-to-cloud platform (also known as HPE GreenLake platform), which supports single sign-on.
In this blog post, I will walk you through the process of configuring Okta Active Directory (AD) to authenticate users into the HPE GreenLake for Private Cloud Enterprise application on the HPE GreenLake platform using SAML Identity Provider (IdP) for single sign-on.
Before starting
Please review the HPE GreenLake User Guide to understand how the SAML framework works in the context of HPE GreenLake for Private Cloud Enterprise Services for the HPE GreenLake edge-to-cloud platform.
Configure SSO/SAML applications in Okta
To configure application metadata in Okta, complete the following steps:
- Step 1: Create an Okta SAML application
- Step 2: Configure Sign On settings
- Step 3: Export the SAML 2.0 IdP metadata
- Step 4: Configure the SAML connection in the HPE GreenLake platform
Step 1: Create an Okta SAML application
- Log into the Okta administration console.
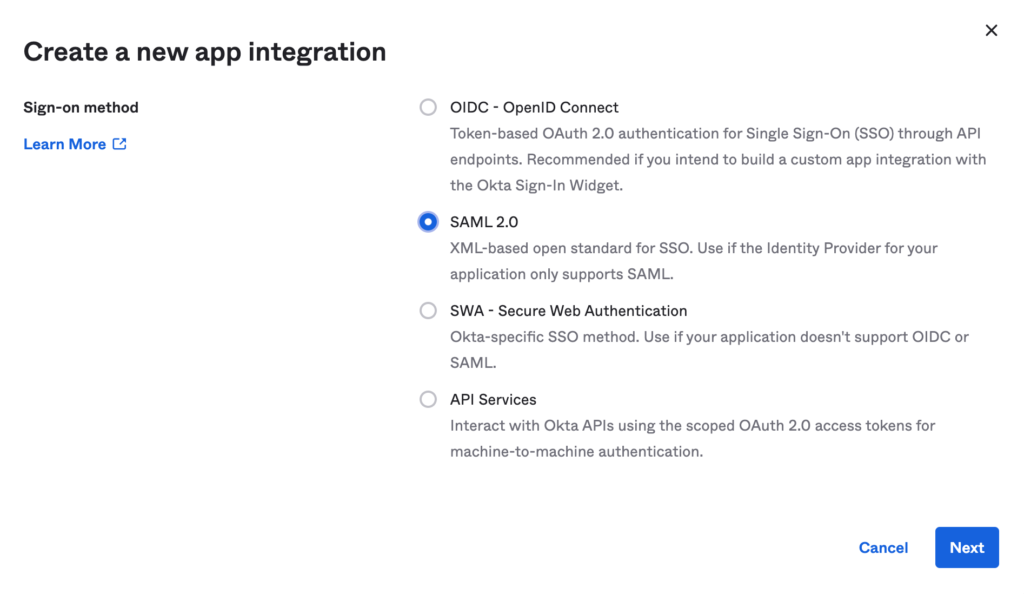
- Click Applications > Create new app integration. The Create a new app integration window opens.
- Select SAML 2.0 and click Next.
Provide a name for the SAML application which gets connected to the HPE GreenLake platform:
Step 2: How to configure single sign-on settings
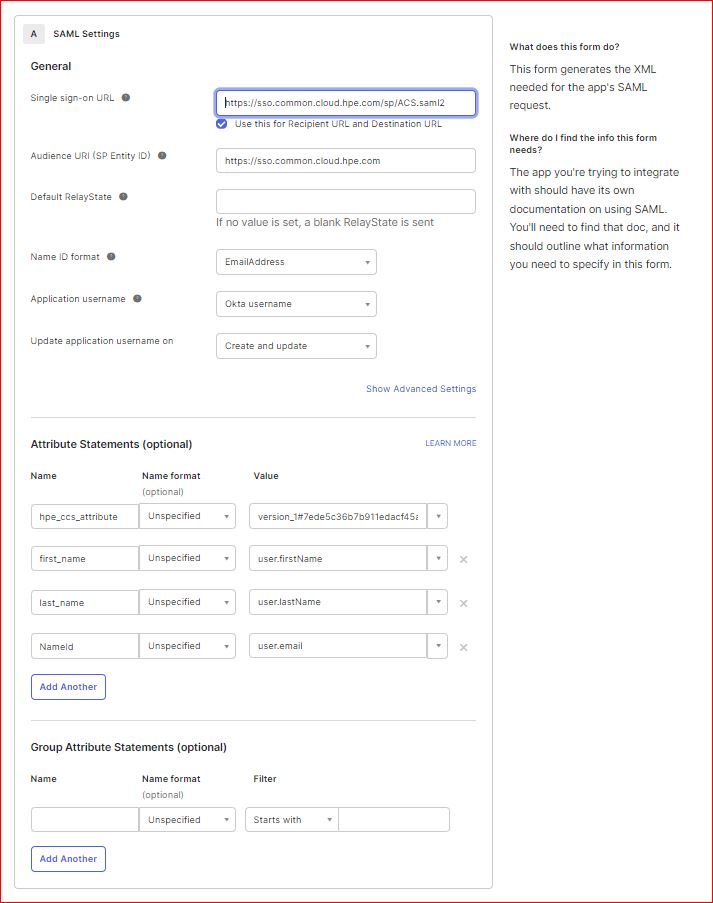
Enter the SAML information.
Under General:
Single Sign on URL: https://sso.common.cloud.hpe.com/sp/ACS.saml2
Audience URI (SP Entity ID): https://sso.common.cloud.hpe.com
Name ID format EmailAddress
Application username Email
NameID = user.email
gl_first_name = user.FirstName
gl_last_name = user.LastName
hpe_ccs_attribute = (See Below)
See here for IdP attribute details: https://support.hpe.com/hpesc/public/docDisplay?docId=a00120892en_us&page=GUID-D7192971-EF71-4304-B51E-548E7954E644.html
A new SAML attribute has been added “hpe_ccs_attribute” which tells HPE GreenLake platform and HPE GreenLake for Private Cloud Enterprise application the exact role/permissions for each user. The following describes how to format the attribute.
Format: {version}#{pcid}:{app id}:{role_name}:{ALL_SCOPES}Note : At present HPE GreenLake for Private Cloud Enterprise application role should be excluded.
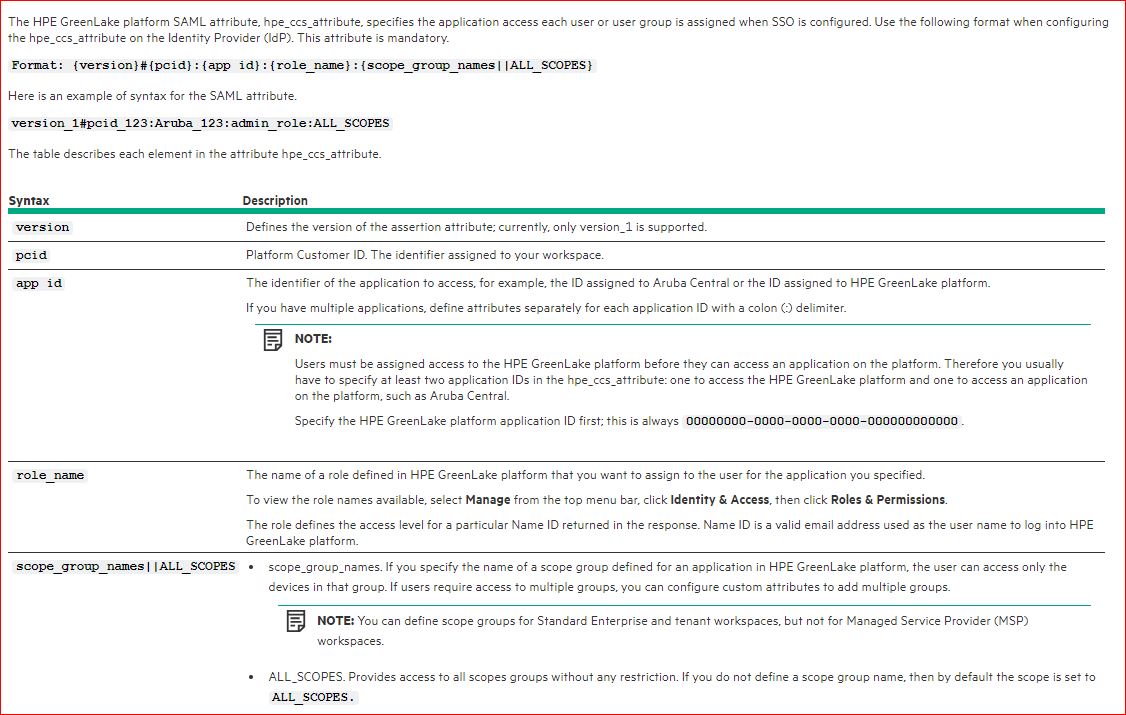
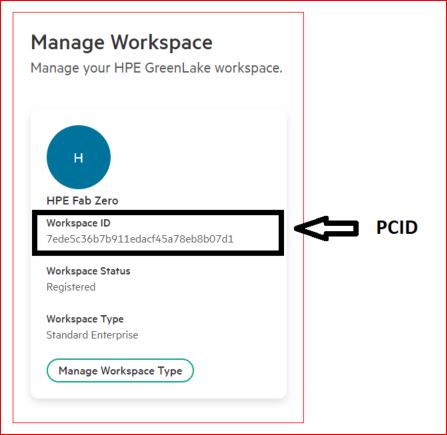
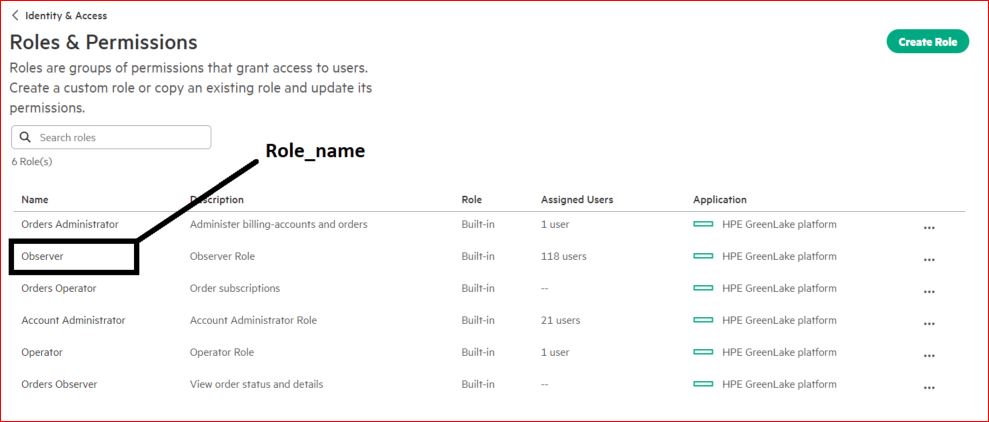
The hpe_ccs_attribute always starts with version1#. You must first configure the attributes for HPE GreenLake platform and to do so, enter the Platform Customer ID (PCID) for the account (this is the identifier assigned to your HPE GreenLake platform Workspace), followed by the HPE GreenLake platform application ID. This will always be 00000000-0000-0000-0000-000000000000. Following this, enter the role name and ALL_SCOPES.
Example:
version_1#7ede5c36b7b911edacf45a78eb8b07d1:00000000-0000-0000-0000-000000000000:Observer:ALL_SCOPES
2. Complete the setup.
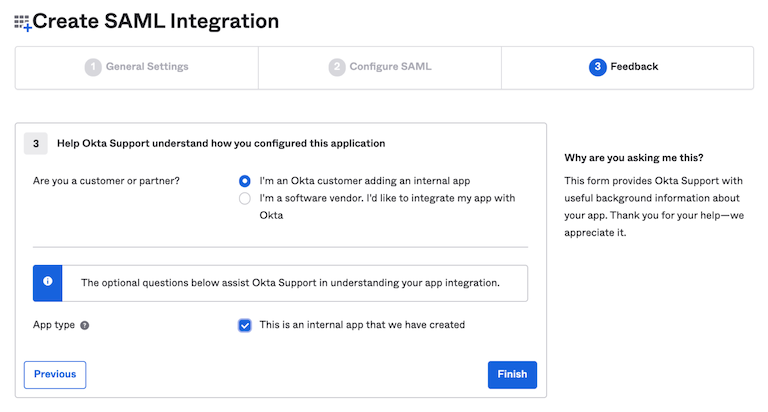
Click Next and select Internal App, then Finish.
Step 3: Export the SAML 2.0 IdP metadata
Click Next – Configure the single sign-on settings
You will find two options are available: View Setup Instructions which steps you through the SAML configuration and Identity Provider metadata, which will produce an XML file that can be loaded into HPE GreenLake platform application.
Suggestion: click Identity Provider metadata and save the XML data to a file.
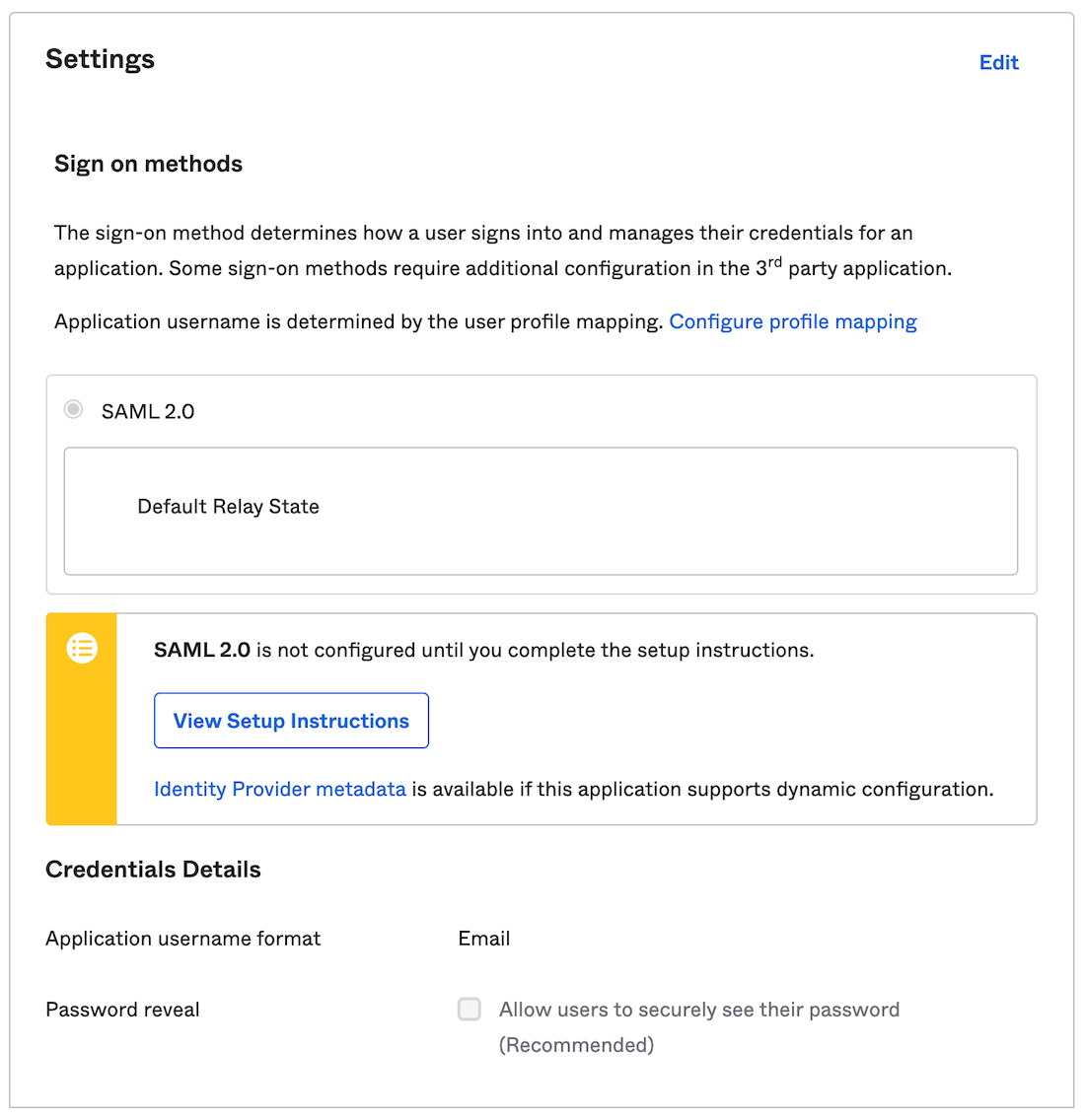
- Click Next.
Select Internal app, and click Finish.
Step 3.1 : Access to the SAML application and HPE GreenLake platform is determined by assigning only those members or group to the SAML application.
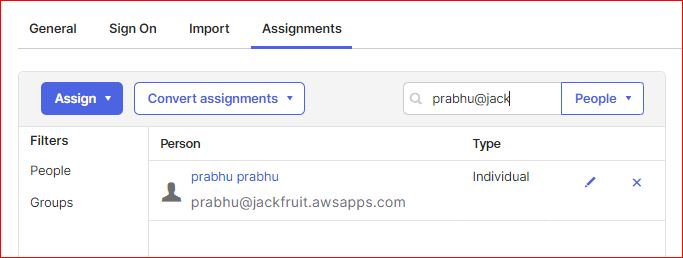
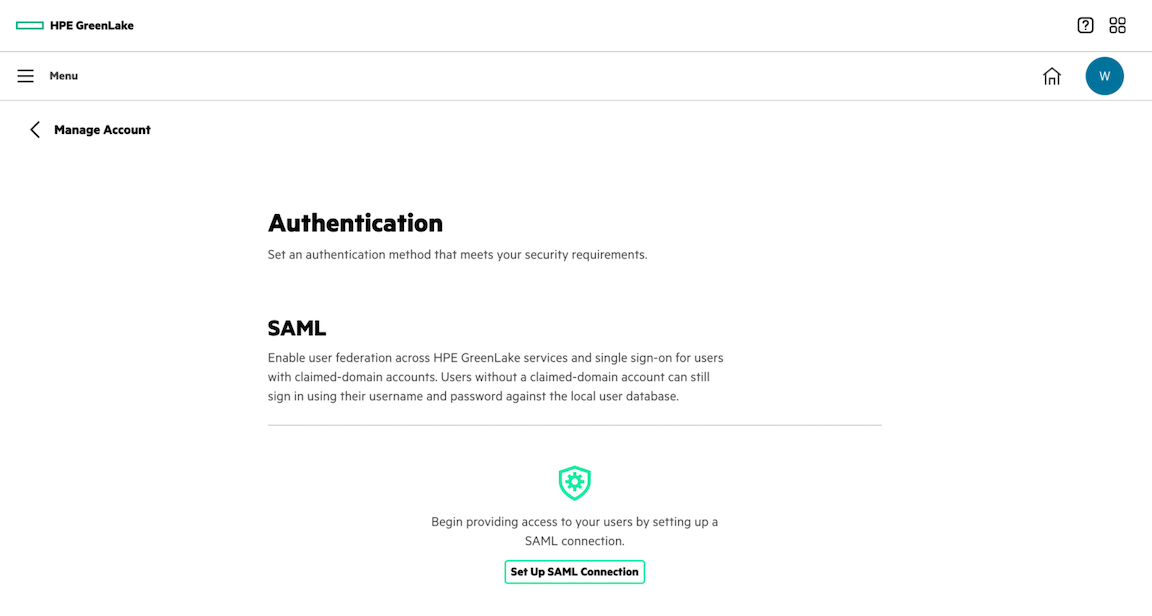
Step 4: Configure the SAML connection in the HPE GreenLake platform
Log into HPE GreenLake platform and click Menu > Manage > Authentication and click Set Up SAML Connection.
Before you can add a new SAML configuration, you must have at least one user account with that domain already enabled in HPE GreenLake platform. Also, you must be logged into HPE GreenLake platform with an account from that domain in order to enable SSO for it.
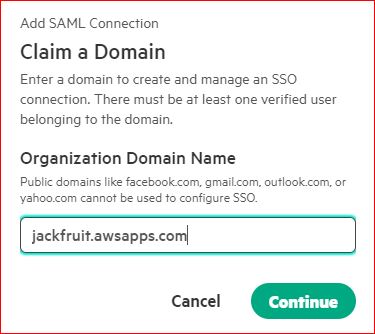
Type in the domain you want to enable SSO on:
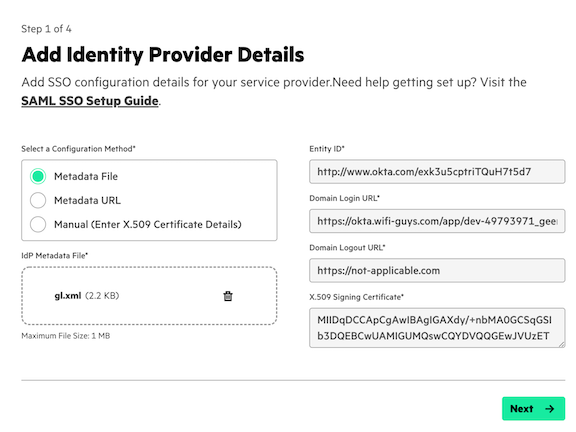
Input the metadata from the step above.
While HPE GreenLake platform does support entering this information manually, it's recommended that you simply upload the XML metadata that was downloaded in the previous step. To do so, select Metadata File, selecting the XML file. Then, click Next.
Enter the SAML attributes to match what was entered in Okta. Set the idle timeout value as well.
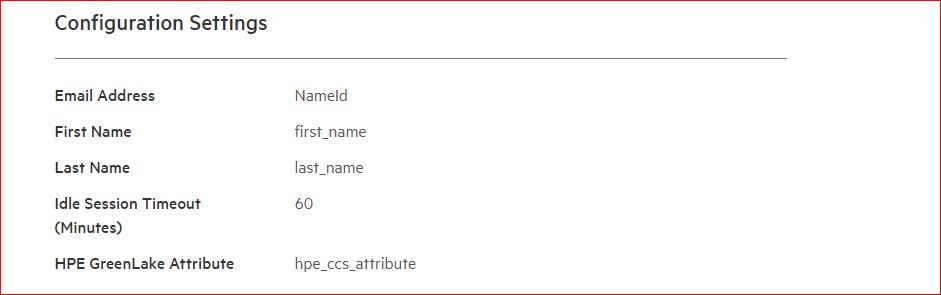
- Then click Next.
Create a recovery user so that, in the event SSO fails, an admin will still be able to access the HPE GreenLake platform.
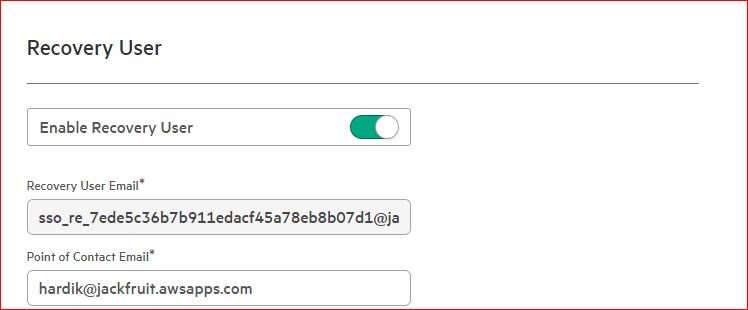
Congratulations! SSO will now be enabled for HPE GreenLake platform as well as the HPE GreenLake for Private Cloud Enterprise application. Log out and on the HPE GreenLake platform home page, click Sign in with SSO.
Testing and troubleshooting:
On the HPE GreenLake edge-to-cloud platform home page, click Sign In with SSO.
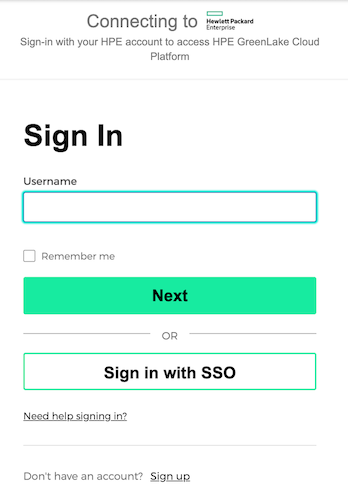
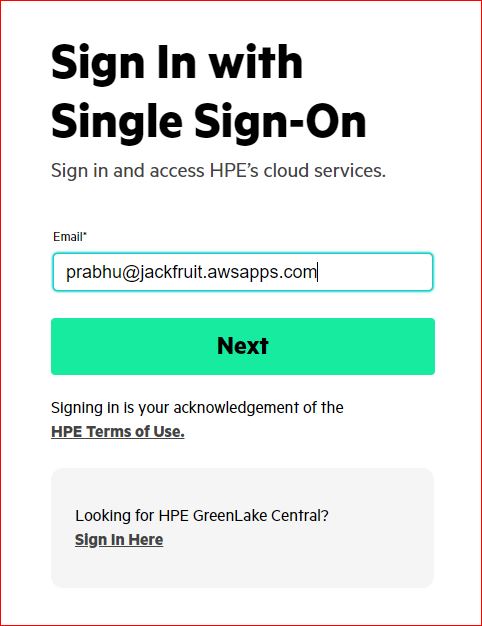
Enter the SSO credentials. You will be redirected to Okta to authenticate. Once you successfully authenticate, you will be redirected back to HPE GreenLake platform. You can then click on the HPE GreenLake for Private Cloud Enterprise application and be given access based on the configured role/permissions.
Additional notes:
- There must be at least one verified user belonging to the Domain prior to configuration.
- In order to configure SSO, you must be logged into the HPE GreenLake edge-to-cloud platform with a user from the domain.
- SSO user access is determined by the “role_name” attribute included in the SAML hpe_ccs_attribute provided by the IdP.
- For more troubleshooting: https://support.hpe.com/hpesc/public/docDisplay?docId=a00120892en_us
- Customer users should be given access to SAML application.
- After authentication when clicking the HPE GreenLake for Private Cloud Enterprise application, if it leads to the below error, it will take 1 hr to sync. If it does not do so within that time period, the customer should contact their HPE administrator.
I hope this blog post answers any questions you may have had in regards to how to configure single sign-on for HPE GreenLake for Private Cloud Enterprise on the HPE GreenLake platform using Okta Active Directory. Please return back to the HPE Developer Community blog for more tips and tricks on working with the HPE GreenLake platform.
Related
Automate ITOps: announcing foundational APIs for the HPE GreenLake edge-to-cloud platform
Dec 1, 2023
Bulk onboarding of users in HPE GreenLake edge-to-cloud platform
Apr 24, 2024Get started with the foundational APIs for the HPE GreenLake platform – Part 1: Introduction to the APIs
Jan 12, 2024Get started with the foundational APIs for the HPE GreenLake platform – Part 2: Configuring and managing a workspace
Jan 31, 2024Get started with the foundational APIs for the HPE GreenLake platform – Part 3: Tracking activities and monitoring health
Feb 2, 2024
Getting started with Private Cloud Business Edition APIs
May 13, 2024