Configuring Azure AD as the SAML IDP with HPE Greenlake Cloud Platform and Aruba Central
July 11, 2022Single sign-on (SSO) enables users to securely authenticate with multiple applications and websites by logging in only once using just one set of credentials (username and password). With SSO, the application or website that the user is trying to access relies on a trusted third party (identity provider) to verify that users are who they say they are.
Azure Active Directory (Azure AD) is a cloud-based identity and access management service that helps you access external resources, such as Microsoft 365, the Azure portal, and thousands of other SaaS applications. Aruba Central uses Security Assertion Markup Language (SAML) identiy provider (idP) to issue authentication assertions in conjunction with a single sign-on profile. In this blog post, I'll explain the process for configuring Azure AD to authenticate users into the HPE GreenLake Cloud Platform (HPE GLCP) and Aruba Central using SAML idP.
I'll explain the process for configuring Azure AD to authenticate users into HPE Greenlake Cloud Platform (HPE GLCP) and Aruba Central using SAML idP.
If you're looking for the Okta version of this information, it can be found on WIFI-GUYS
Contents
- Before you Begin
- Terms used in this blog post
- Steps to Configure SSO/SAML Application in Azure AD
- Step 1: Create an Azure AD Enterprise Application
- Step 2: Configure GCLP for SAML Federation
- Login to HPE GLCP and Aruba Central using Azure AD
- Using Azure AD MFA
- Troubleshooting
- Appendix: Generating the hpe_ccs_attribute
Before you Begin
This blog post references the following documentation:
If you're looking for the Central 2.5.4 SAML integration guide, it has been moved.
Terms used in this blog post
- CCS: Common Cloud Service
- GLCP: HPE GreenLake Cloud Platform
- SSO: Single Sign On
- SAML: Security Assertion Markup Language
- idP: Identity Providers
- AD: Active Directory
- MFA: Multi-Factor Authentication
- MSP: Managed Service Proivder
- XML: eXtensible Markup Language
Steps to Configure a SSO/SAML Application in Azure AD
To configure SSO in Aruba Central, first download the metadata file from Azure AD.
- Create an Enteprise Application in the Azure Portal
- Configure the Enterprise Application for HPE GLCP
- Download the federated metadata XML file from Enterprise Application
- Claim and configure your domain within HPE GLCP
- Upload the federated metadata XML file to HPE GLCP
- Create a recovery account
Step 1: Create an Azure AD Enterprise Application
Log into to the Azure portal.
Click Enterprise Applications (you may need to search for it, if it's not on your menu)
Click New Application
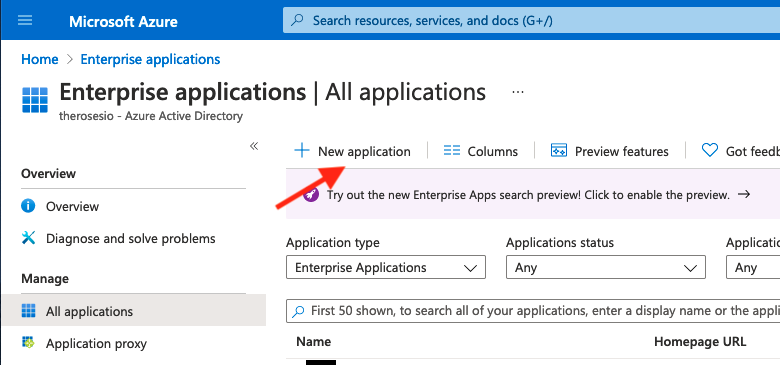
Click Create your own Application
Enter the name of your app. (Ex: Aruba Central USWEST 4)
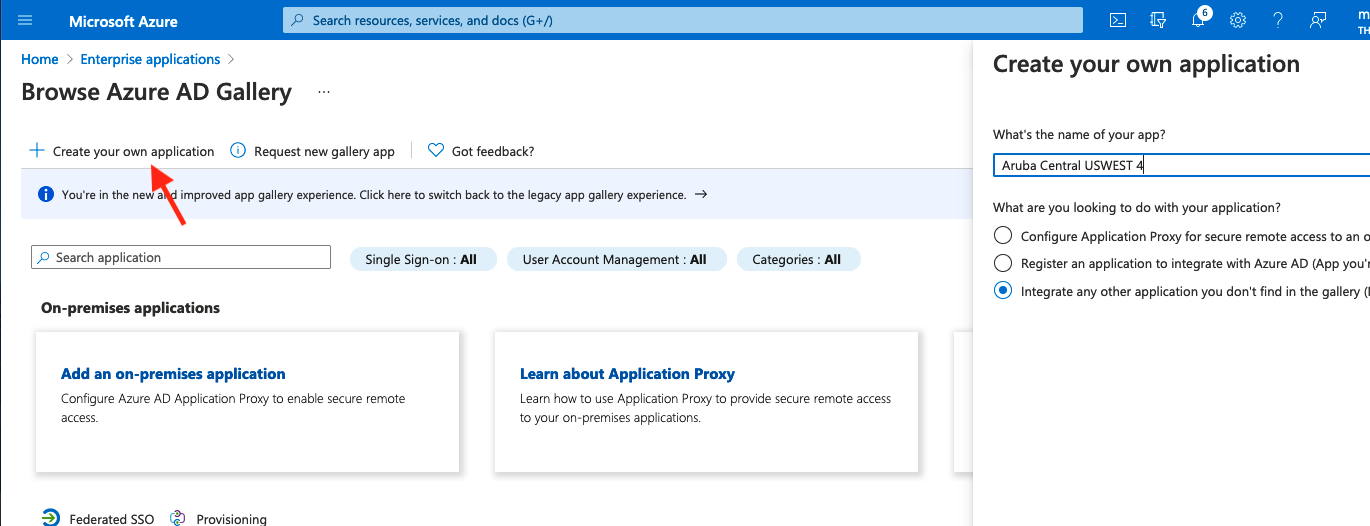
Select Integrate any other application you don't find in the gallery (Non-gallery)
Under Step 1: Assign users and groups, select the AD Group you created at the beginning of this document.
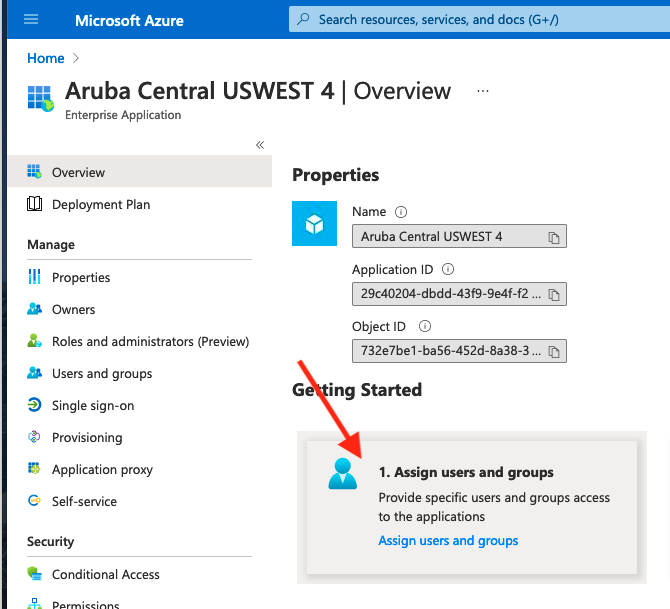
Under Step 2: Set Up Single Sign-On
The default setting is Disabled. Select SAML
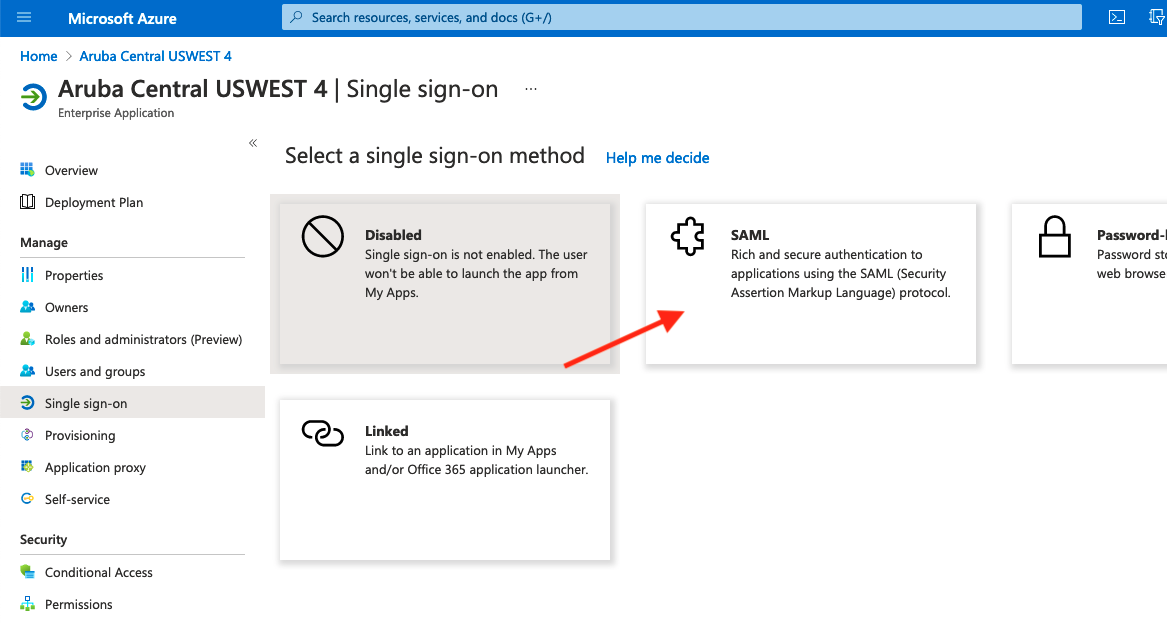
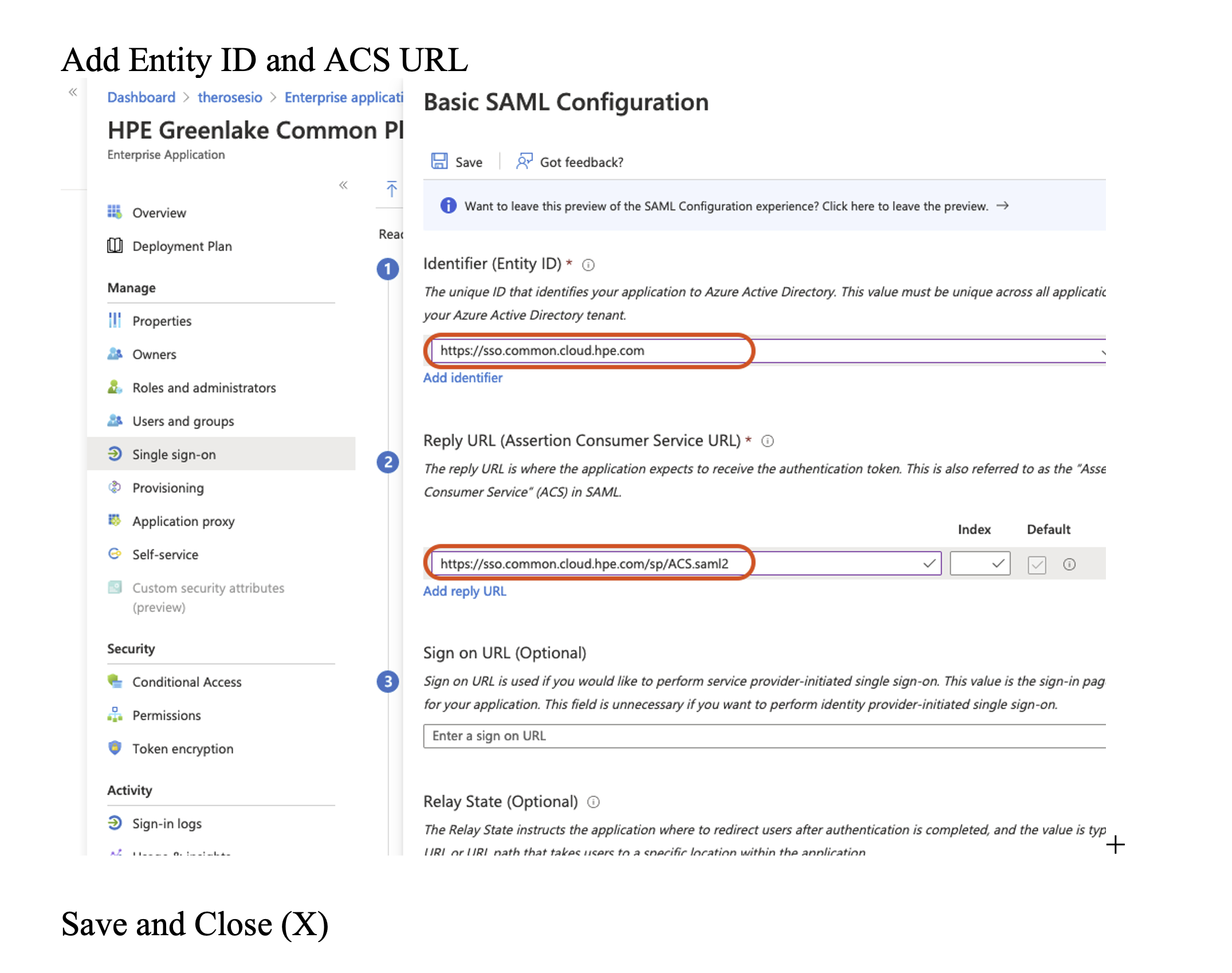
Under Basic SAML Configuration, click Edit
Attribute | Values |
| Identifier (Entity ID): | https://sso.common.cloud.hpe.com |
| Reply URL (Assertion Consumer Service URL): | https://sso.common.cloud.hpe.com/sp/ACS.saml2 |
Under Attributes & Claims
AttributeValueemailaddress user.givenname name user.userprincipalname gl_first_name user.givenname gl_last_name user.surname hpe_ccs_attribute See Below version_1#2fd5f97acbc211ecadc006baf610dd36:00000000-0000-0000-0000-000000000000:Account Administrator:ALL_SCOPES:683da368-66cb-4ee7-90a9-ec1964768092:Aruba Central Administrator:ALL_SCOPESWhere the PCID (2fd5f97acbc211ecadc006baf610dd36) is your ID for HPE GLCP and App ID (683da368-66cb-4ee7-90a9-ec1964768092) for your Central clusterFor more details on the
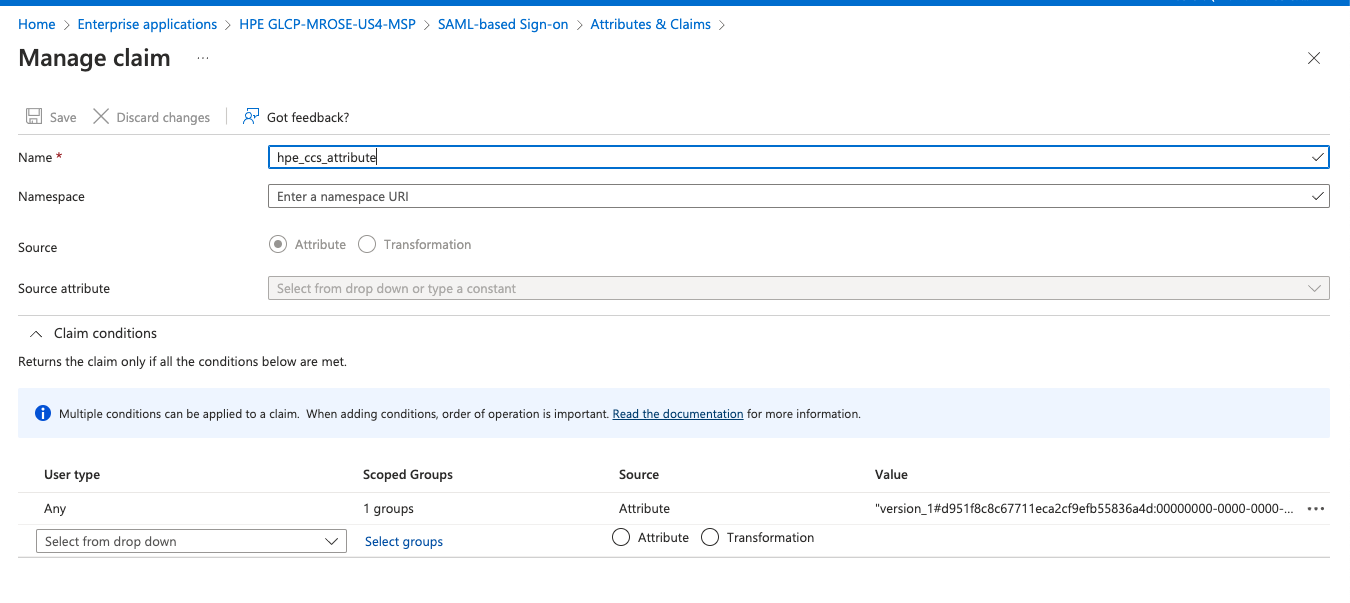
hpe_ccs_attritube, see the Appendix: Generating thehpe_ccs_attribute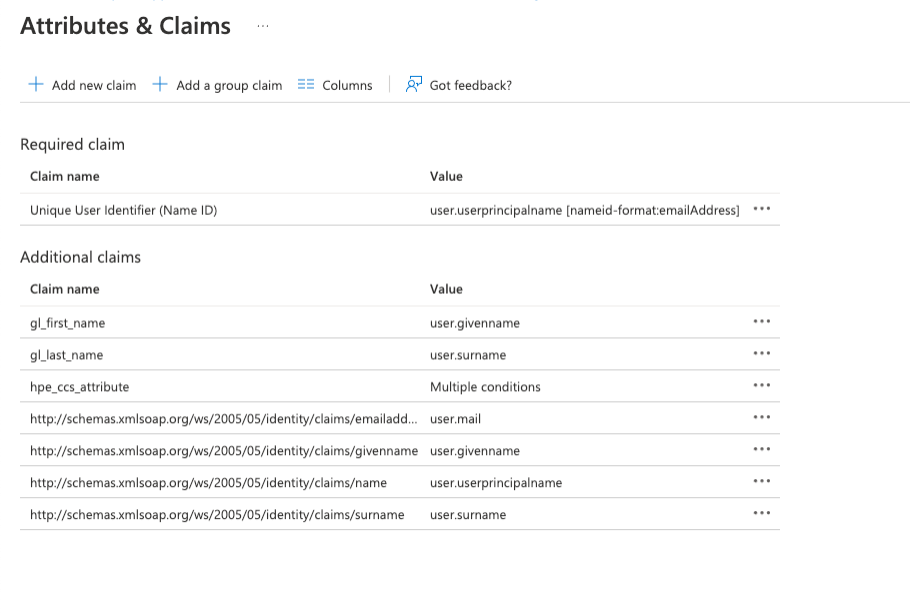
Click Download under Step 3 : Federation Metadata XML.
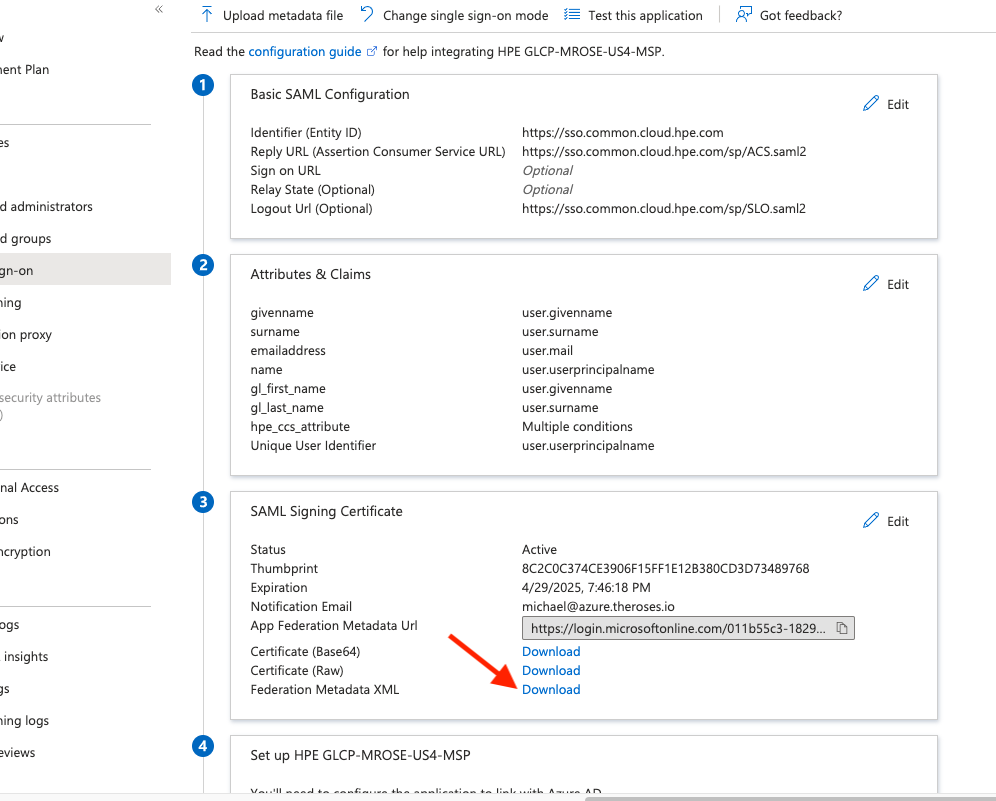
Step 2: Configure GCLP for SAML Federation
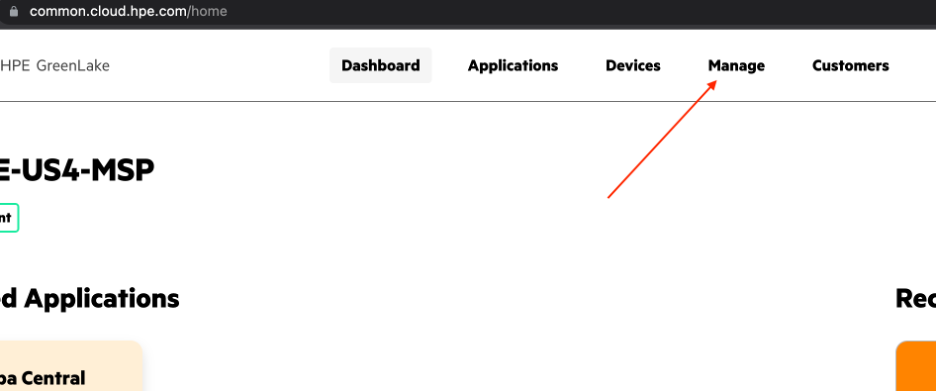
Login to HPE GLCP and select Manage.
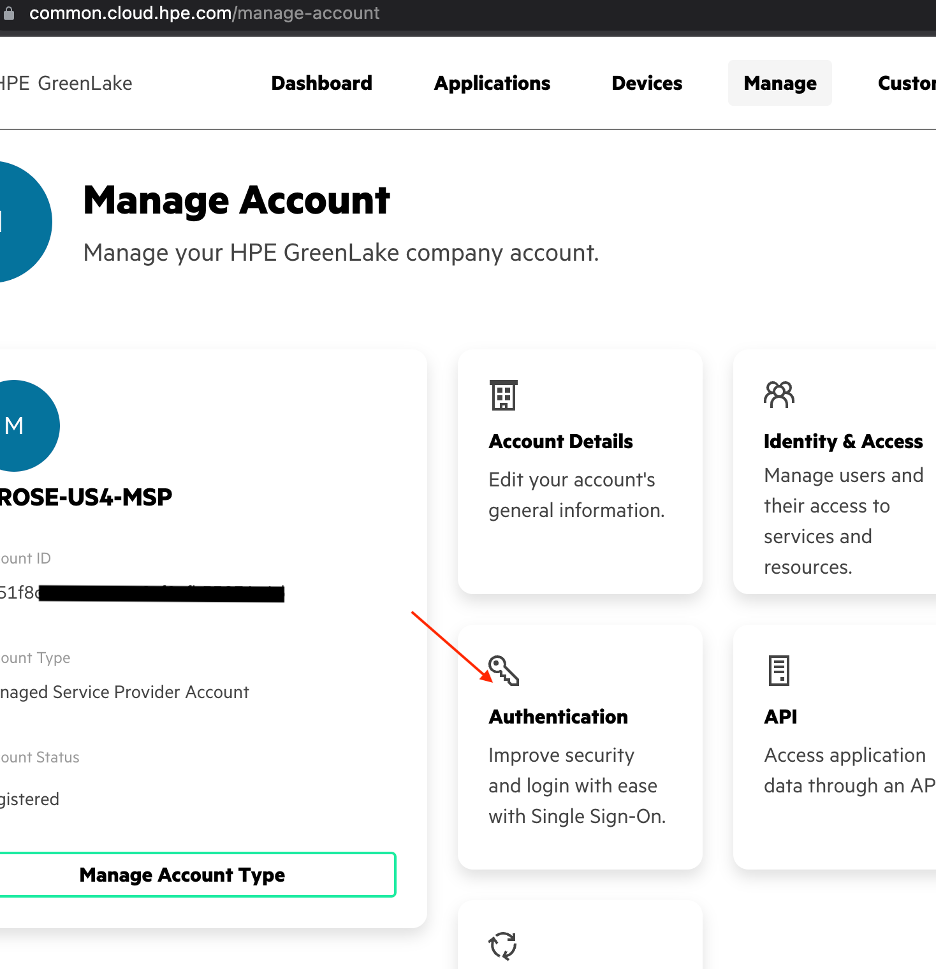
Select the Authentication tile.
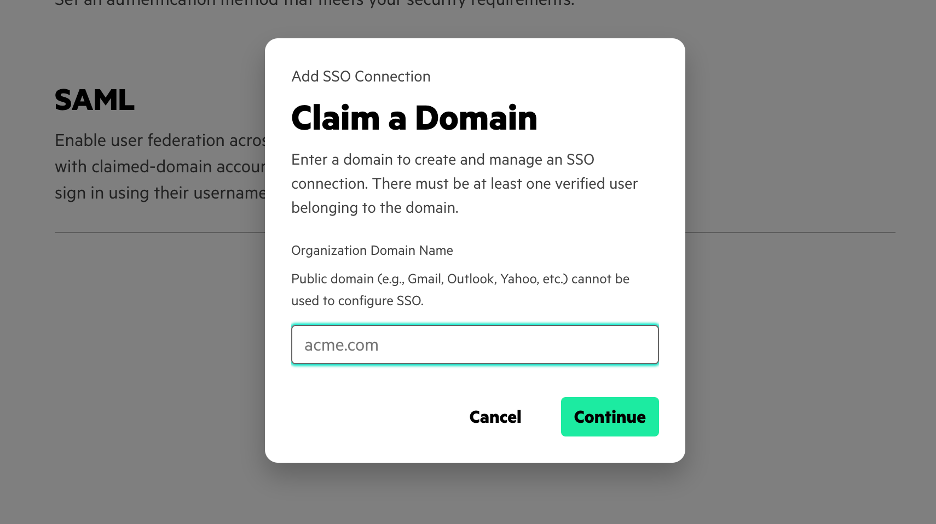
Claim your domain for SAML.
Upload the Federation Metadata XML file from the previous section.
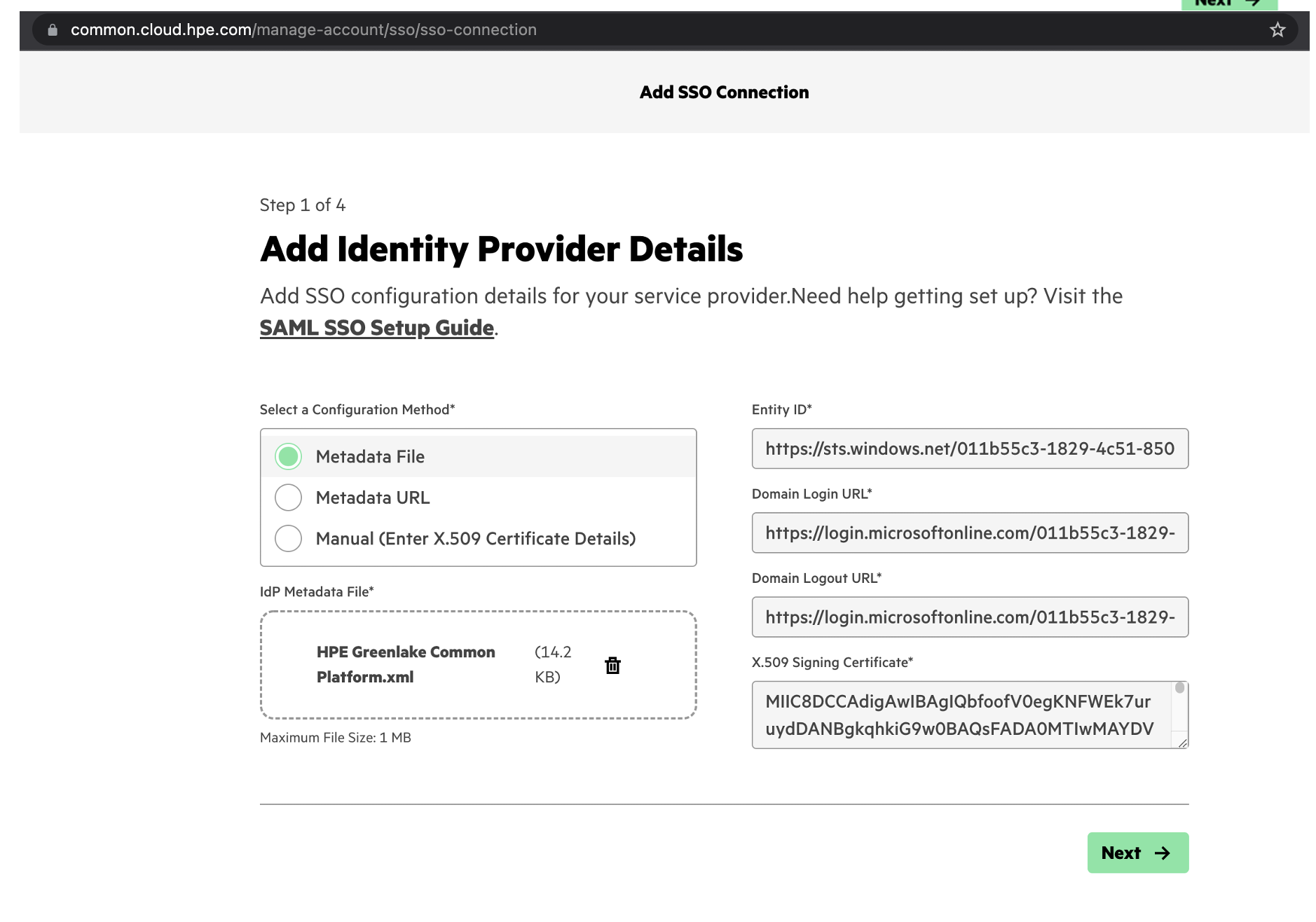
Apply the following configuration settings. These should match the First and Last Name settings you set above for Azure.
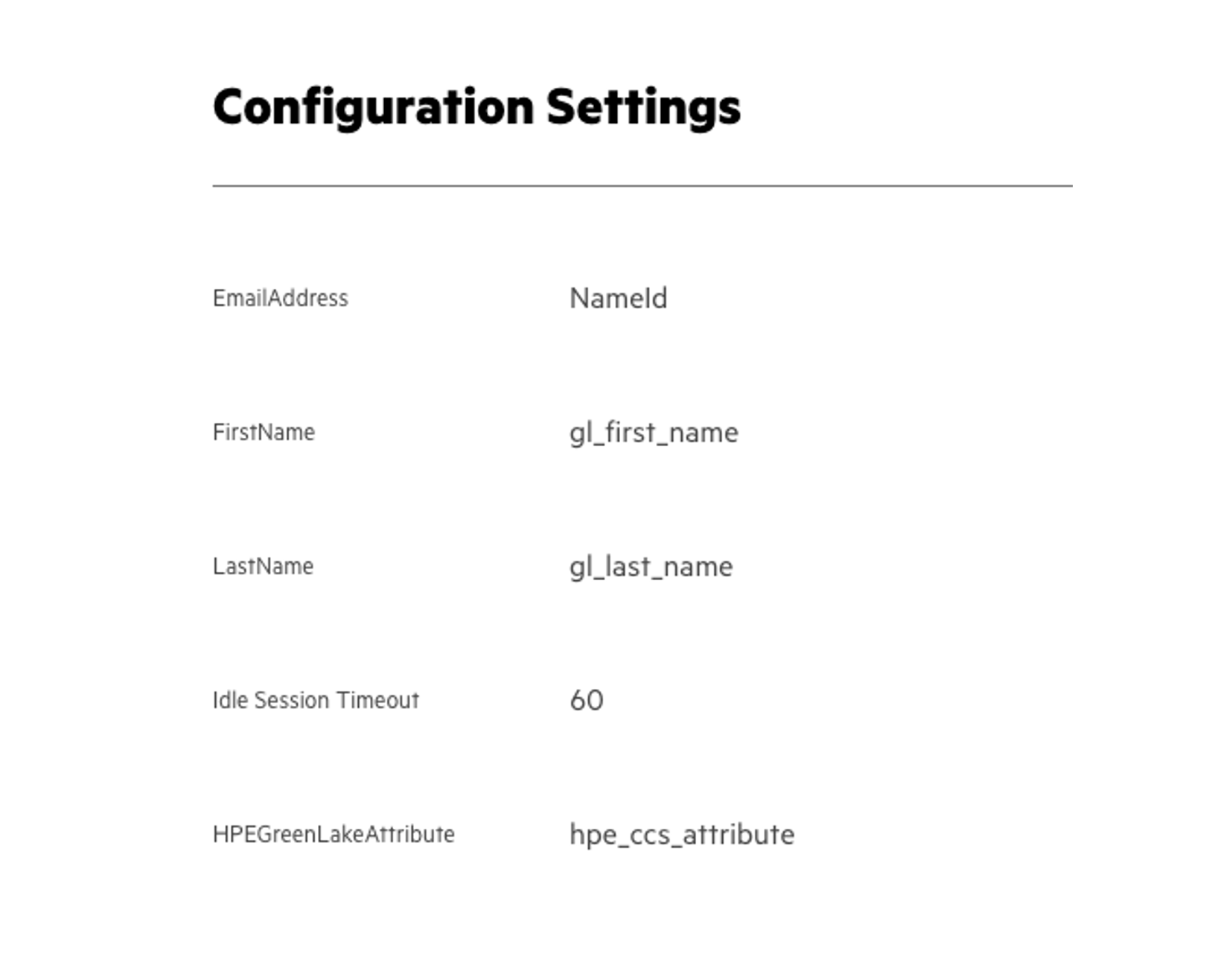
Create the recovery user per the instructions.
Validate the settings are correct.
Save and finish the configuration.
If you get an error that the SAML configuration wasn't completed using the account with the @domain.com, you'll have to log out and login again with the SAML domain and go through the above configuration again.
Log in to HPE GLCP and Aruba Central using Azure AD
Once you've completed the above steps, log in to HPE Greenlake Central using your Azure AD email.
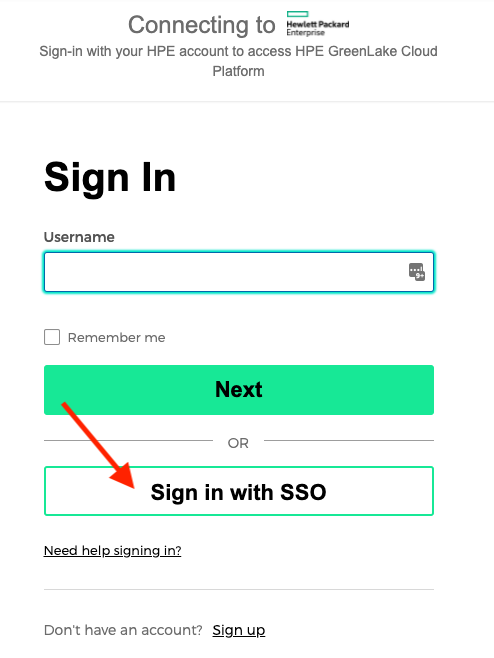
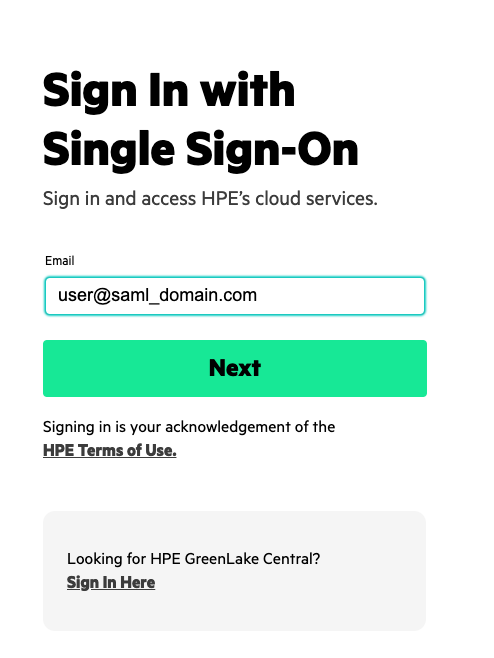
If everything is working correctly, you should have logged into HPE GLCP and find the Aruba Central application tile with an button to "Launch" the Aruba Central application.
Using Azure AD MFA
By default, Azure AD enables Multi-Factor Authentication (MFA). However, for testing and demos, it's much easier to disable MFA on your accounts. To disable MFA, please see the following documentation: What are security defaults
Troubleshooting
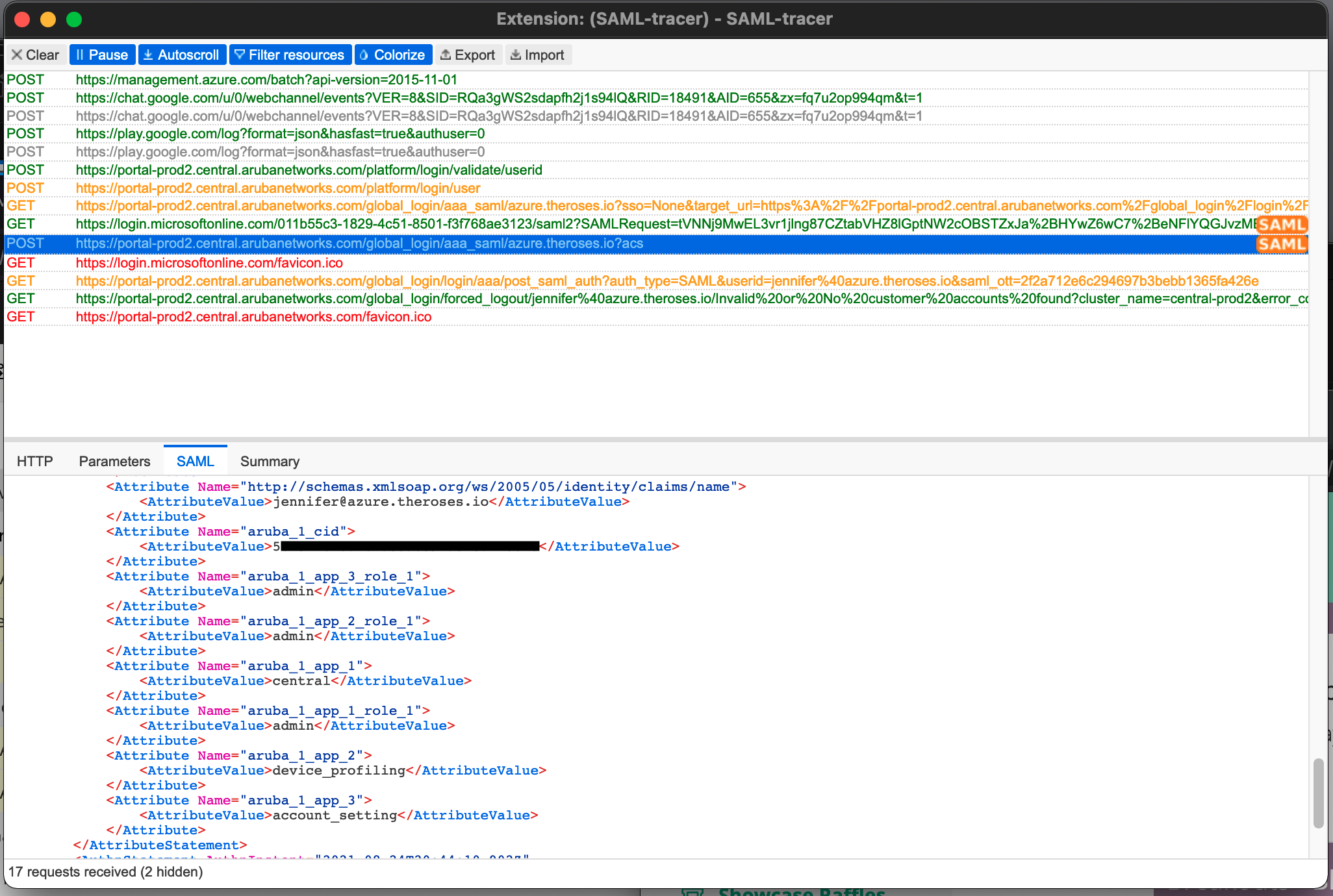
There's a useful 3rd-party browser tool called: SAML Tracer
This tool will allow you to verify the attributes you're sending to Central.
It can be useful when configuration SAML with multiple HPE Greenlake Central accounts or domains.
Appendix: Generating the hpe_ccs_attribute
The hpe_ccs_attribute is used to determine your HPE GLCP account. The format for the hpe_ccs_attribute is as follows:
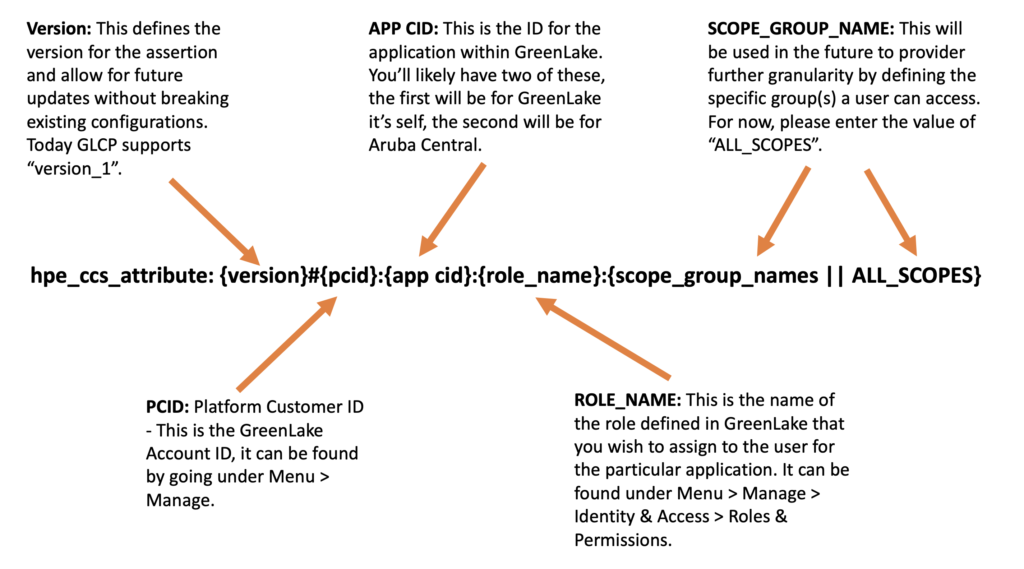
An example hpe_ccs_attribute for a single HPE GLCP and Aruba Central account would be:
version_1#2fd5f97acbc211ecadc006baf610dd36:00000000-0000-0000-0000-000000000000:Account Administrator:ALL_SCOPES:683da368-66cb-4ee7-90a9-ec1964768092:Aruba Central Administrator:ALL_SCOPES
or
version_1#5b0ec0e8b4f411eca432ba72799953ac:00000000-0000-0000-0000-000000000000:Account Administrator:ALL_SCOPES:683da368-66cb-4ee7-90a9-ec1964768092:Aruba Central Administrator:ALL_SCOPES#5b0ec0e8b4f411eca432ba72799953ac:00000000-0000-0000-0000-000000000000:Account Administrator:ALL_SCOPES
If you're a Managed Service Provider (MSP), then the hpe_ccs_attribute for Administrator rights to HPE GLCP and Aruba Central for all customer tenant accounts is as follows:
version_1#d951f8c8c67711eca2cf9efb55836a4d:00000000-0000-0000-0000-000000000000:Account Administrator|TENANT|:ALL_SCOPES:00000000-0000-0000-0000-000000000000:Account Administrator|MSP|:ALL_SCOPES:683da368-66cb-4ee7-90a9-ec1964768092:Aruba Central Administrator|TENANT| : ALL_SCOPES:683da368-66cb-4ee7-90a9-ec1964768092:Aruba Central Administrator|MSP| : ALL_SCOPES
The hpe_ccs_attribute string for a tenant under a MSP account is shown below. Please note, you must have the SAML domain configuration configured for that tenant account using the same setting as the MSP account. To say it another way, you must go through this configuration for each tenant account under the MSP.
version_1#f9ee1cdecc1611ecb00e9e24ed17d2a7:00000000-0000-0000-0000-000000000000:Observer|TENANT| :ALL_SCOPES:683da368-66cb-4ee7-90a9-ec1964768092:Aruba Central Administrator|TENANT| :ALL_SCOPES
Conclusion
In this blog post, you learned how to configure Azure AD with HPE Greenlake by passing the necessary configuration and customizations using the hpe_ccs_attribute. From this point, you can create custom attributes to grant different level of access based on roles such as Read/Write or Read/Only access.
If you have feedback to this blog post, please send me a message.
Be sure to come back to the HPE Developer Community blog for more articles on this and other interesting subjects.
Related

Configuring SSO for Aruba Central and HPE GreenLake using Okta
Mar 26, 2024
VLAN Versus VXLAN
Nov 18, 2024A guide to enabling a managed Istio service mesh in a Kubernetes cluster on HPE GreenLake for Private Cloud Enterprise
Feb 16, 2023Using HPE GreenLake Console's API Gateway for Data Services Cloud Console
Nov 30, 2021Automate ITOps: announcing foundational APIs for the HPE GreenLake edge-to-cloud platform
Dec 1, 2023
Bare metal provisioning on HPE GreenLake using Terraform
Mar 20, 2023